While all VPNs claim to not log traffic information, there is one major difference between us and others.
Because other VPNs are built on Linux and software, it IS possible to look at the traffic in real time. Any IT engineer with admin access can login to the servers and run a simple command like “tcpdump”, and see exactly what every VPN user is doing. See example of tcpdump output from Wikipedia below.
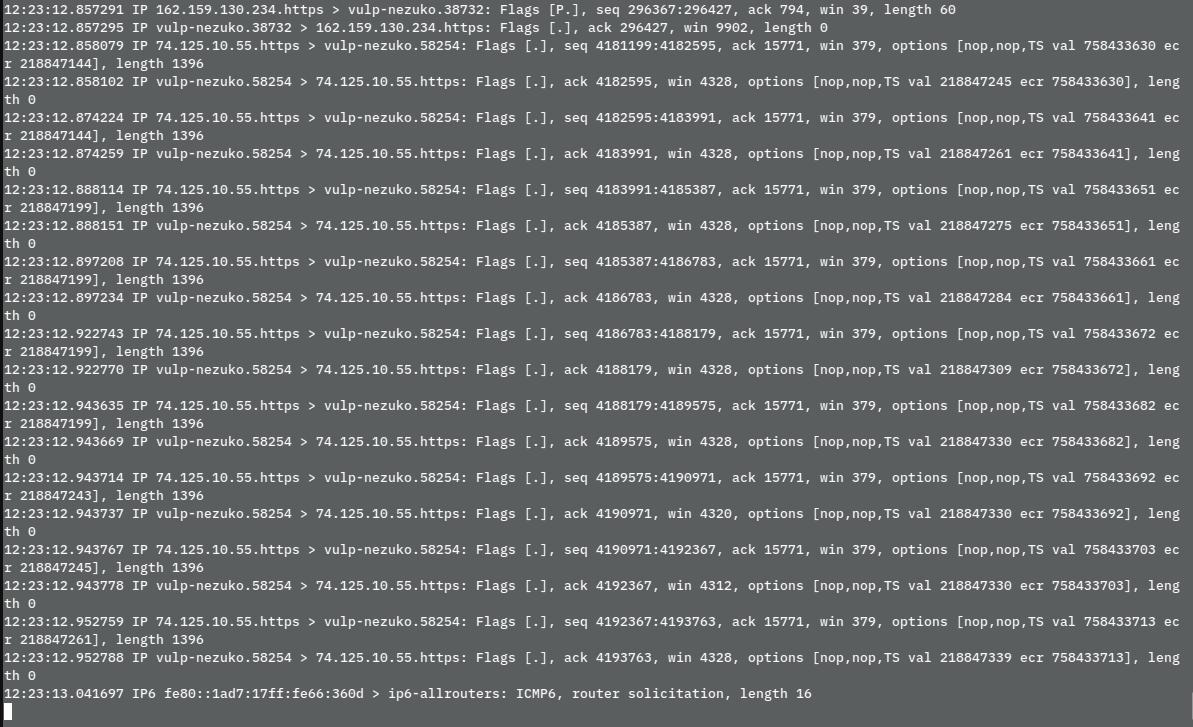
Reflect on this for a second. Many VPN users are using a VPN to avoid that their ISP (Internet Service Provider) can see what they do online (which websites they visit), searches they do, etcetera. But if instead the VPN provider, and the cloud provider that the VPN provider uses, have access, then what good is it to use the VPN? The privacy issue has only moved elsewhere. True, your ISP can no longer see you, but your VPN provider can instead.
How Hidden24 is different
We are radically different here. After we have configured one of our hardware machines in our data centre, we discard the key. After a completed configuration, no one in the entire world – not even our own engineers – can access the machine again. If we need to change a configuration, we need to first erase everything and start from scratch. For clarity: we cannot login to our own machines as admin, after we have started using them.
Back to Comparison: How Hidden24 is different from other VPNs