Most VPNs use Linux together with software such as OpenVPN and Strongswan on the server side. While open source is generally reliable, there are severe disadvantages with this kind of solution.
1) It needs configuration, and configuration can be setup insecurely by mistake.
2) Hackers, and governments, are constantly looking for new attack vectors to common software platforms. And using many different software layered together stacks, means that there are many different attack vectors for hackers to explore.
3) On servers there are hard drives where information gets stored permanently.
4) There are various levels of admin access to a server, than can be exploited.
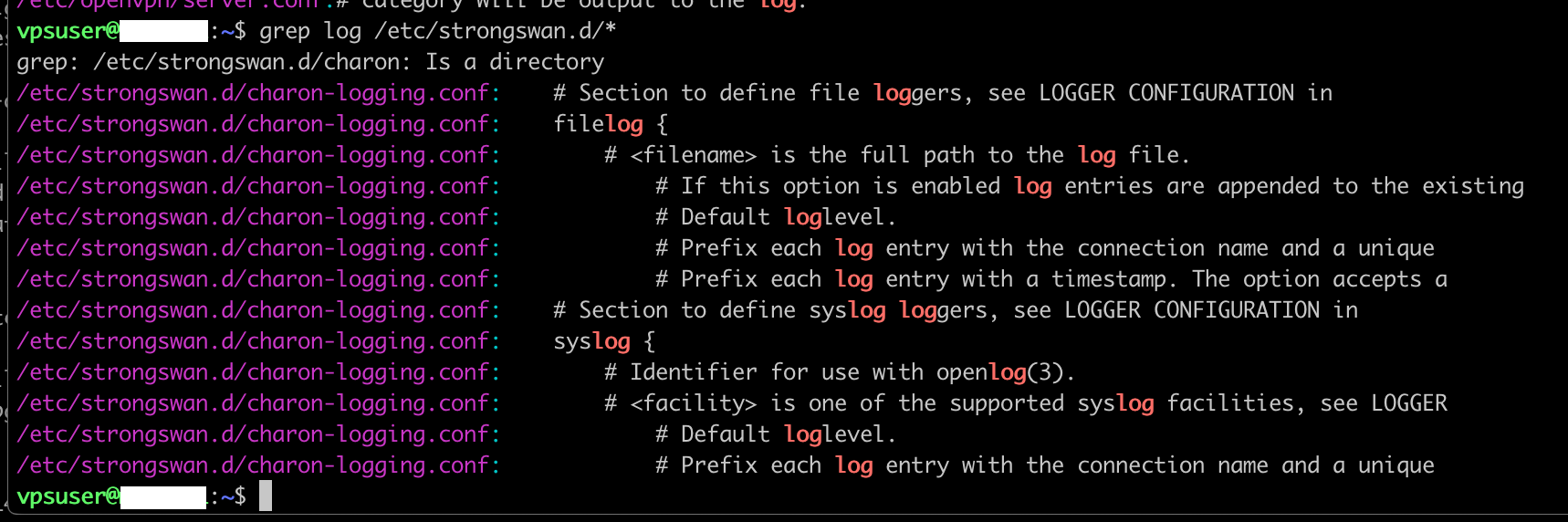
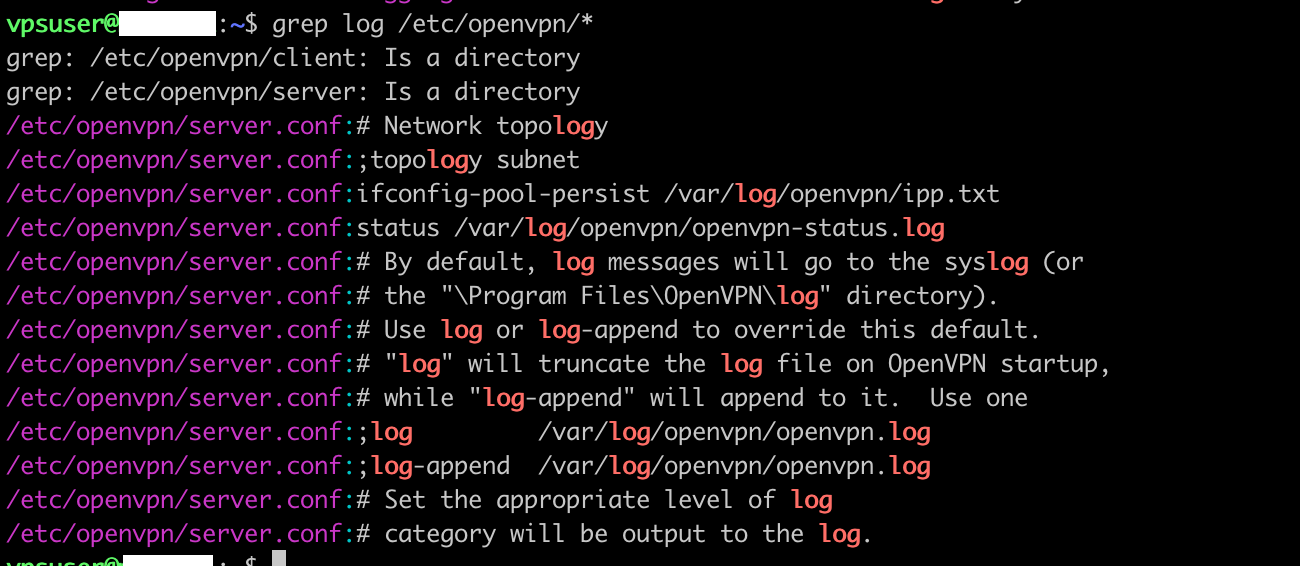
5) With software, it is possible to configure logging.
The complexity of software configuration is … complex. Look for example at the screenshots below, showing the configuration options for logging in Strongswan and OpenVPN. Even if the VPN provider does not activate this logging, the option is still there to do it in the software used. A rouge employee or a hacker have the option to activate logging at a very detailed level.
How Hidden24 is different
We deliver our VPN through a 100% hardware only solution. This means there is no commonly used software, no layers of software that need to work together, no configuration files that can be setup insecurely by mistake. No logging options that can be activated.
Since we use our proprietary code on the hardware, there are no known attack vectors. There is no Linux platform with known issues to exploit.
There are also no hard drives in our solution. When we plug the electricity from one of our machines, everything is simply gone in a blink.
In our view, a hardware-only solution is essential to deliver a fully secure VPN. All VPNs based on a mix of software, are inherently not fully secure.
Back to Comparison: How Hidden24 is different from other VPNs